Why does security energy use 3% of your annual revenue as a assumed ransom? Is this just a random number or is it more significant?
Data from actual cyber-attacks shows that most ransoms are in the 2-5 percent range. This is a good starting point and can be further refined by going through some factors that cybercriminals consider when setting the amount.
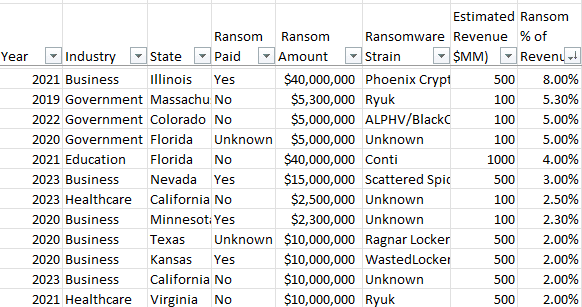
First, think through the motivation of the cybercriminal. They want to get paid quickly. They already went through planning and development and finally got to a ransom stage; now they'd like to get some payoff before you find some other way or else they are disrupted. Mid-single digits of your annual revenue is an amount that you are likely to be able to access within a week. If you are a $10 million dollar a year company and receive a ransom note for $2 million…only in rare circumstances would you have that sitting around in liquid assets, much less something easily converted to Bitcoin. If you get a ransom demand for $300,000, then that is at least feasible should you decide to pay.

Next, the criminal wants to ensure you do decide to pay. The ransom amount must be less than alternatives to the company. If you are ransomed for an amount greater than the cost of restoring or even replacing systems then that's what you'll do. The ransom must be a meaningful amount for the cybercriminal but also an "easy" choice for the victim. If you are asked for too much, you'll just tell them to $%*# off and pay the lesser recovery cost.
3 percent specifically was chosen because this amount works nicely within the overall Fermi estimation. Using a target of 3% revenue and 3% success rate, means that one hour of cybercriminal resources are expanded for every $100,000 target annual revenue. This is a key part of the quantitative side of Security Energy that yields simple roadmaps to effective defenses.
If it's so simple then why are companies still beached?
Not knowing which techniques to focus on. Thinking cyber ninjas are behind every door and defending against whatever threat is on bleepingcomputer today is a great way to become exhausted and still face a ransom note tomorrow. Effective security programs focus on cyber hygiene first and then work their way up the ladder of security energy. Figure out which rung you need to be at and then deny any lower-level criminals the opportunity.
Cyber criminals are able to adapt new techniques, especially so called N-day attacks. Once a technique makes it into the public domain there is no loss of capability if it's discovered so there is a mad rush to use it against as many targets as possible. These can be deployed within hours when most defensive teams will take days to patch. These types of attacks are often low effort per target once they are weaponized and these cases of high impact requiring low influence energy are especially dangerous. You need an equally adaptable external vulnerability management process to counter this.
If you need help with managing external vulnerabilities or evaluating what attacks need to be mitigated, contact security optimizer right now!
