"How do I know if this threat affects me?"
This is the golden question that determines if you'll be staying late tonight securing the network or off early to hit the links.
You can reframe the question into "How much influence energy does the threat represent?" By determining this, you can know if you need to add new countermeasures or it's covered by existing security processes and you can keep working on your to-do list.
One approach to measuring influence energy is to use skill mapping and pre-requisite knowledge. The more skills and pre-requisite knowledge needed to pull off a capability, the higher it's influence energy is.
If a technique, let's say writing phishing emails can be taught to someone with "general computer knowledge" in less than an hour, then it is influence energy 0. Very few cyber techniques fall into this range. Most cyber influence techniques have prerequisite knowledge of advanced computing knowledge and/or other offensive techniques which means there are exponential increases in the number of capabilities as you go from level 0 to 5.
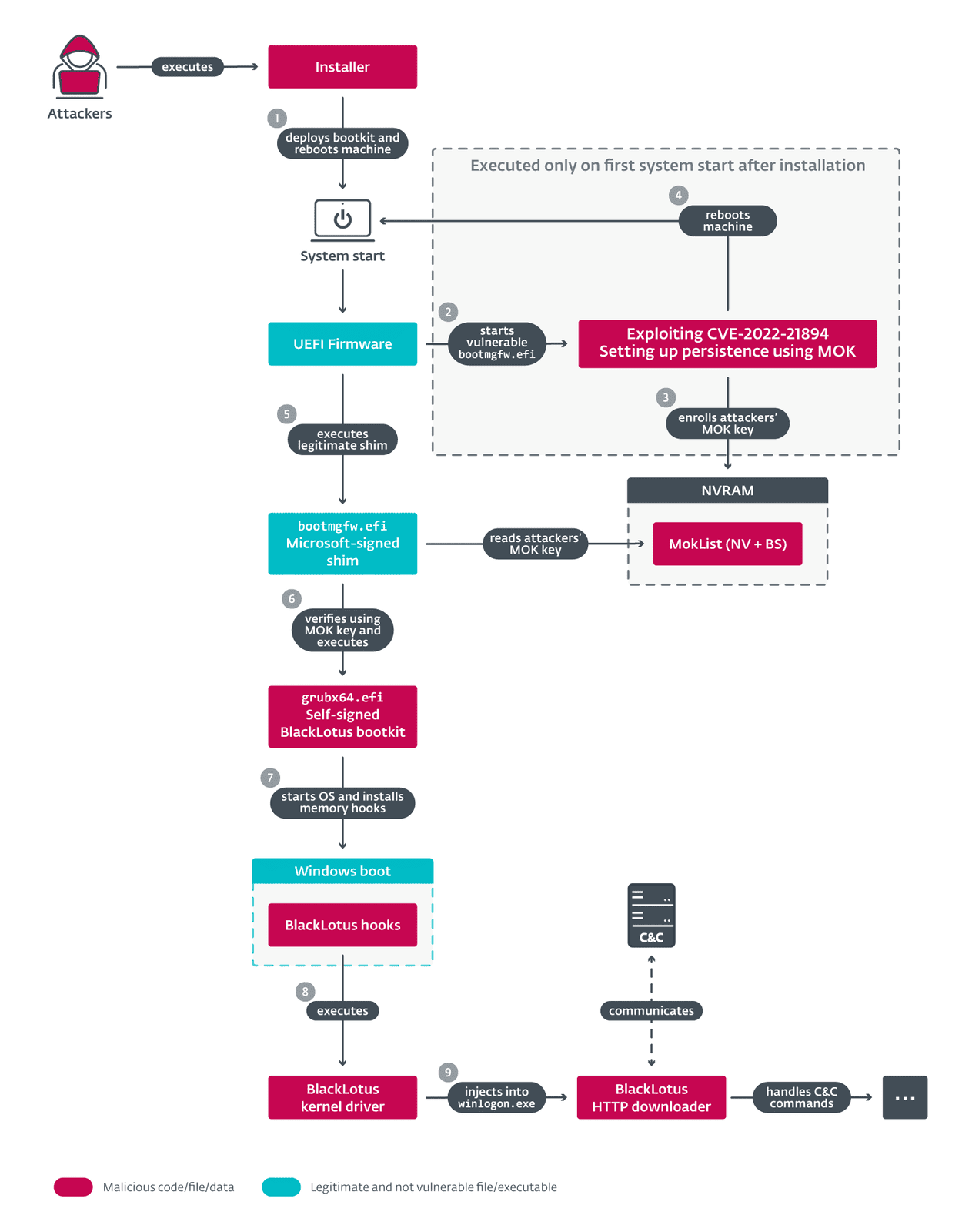
Take a look at the Black Lotus UEFI implant. Looking at the flowchart from the article, you can see the following skills/knowledge needed to create/use such a capability:
- Acquire admin level access to a system
- Creation of EFI binaries
- Knowledge of SecureBoot
- Ability to create exploit binary
- Ability to inject kernel hooks
- Creation of kernel driver
- C2 Infrastructure for it to communicate with
Clearly this list is not teachable within 1 hour so it is higher than IE 0. How far above zero is it?
Next you recursively break down each item in the list and estimate how many hours they would take to teach -- rounding everything to orders of magnitude (1, 10, 100, etc). For things over 10, it is best to break them down into their components.
Acquire admin level access to a system | 1000 |
| Each of these is its own art form |
Creation of EFI binaries | 100 |
|
|
Knowledge of SecureBoot | 10 |
|
|
Ability to create exploit binary | 1000 |
| Each of these is 100 hours at least |
Ability to inject kernel hooks | 1000 |
|
|
Creation of kernel driver | 1000 |
|
|
C2 Infrastructure for it to communicate with | 100 |
|
|
Summing up the elements of this chart, you estimate 4210 hours for this capability. Taking the logarithm of it, results in influence energy 3.6 which means that it doesn't apply to security energy 3 or lower organizations.
By following this simple process, you can analyze threats and know which ones to focus on and which ones to ignore!
