Cyber Analysis Legacy
How does the Security Energy framework relate to the Pyramid of Pain?. This influential analysis of cyber threat intelligence organizes attack attributes according to how difficult they are to change.
If you think this sounds a lot like Influence Energy…you are right! How does each level of the pyramid relate to Influence Energy and what does that mean for how defenders need to act?
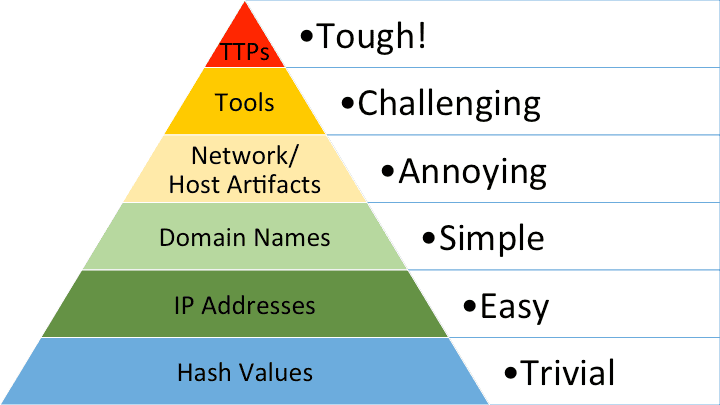
Each layer of the pyramid of pain represents one type of threat intelligence that can be shared with other cyber teams to identify malicious activity. Actionable threat intelligence is a key capability of security energy at lower levels because the more prevalent an attack is, the less likely you are to be the first victim. Known bad files or domain names can then be blocked with basic antivirus software and internet access controls.
The first level of the pyramid is file hash values which comprise the majority of cyber threat intelligence. In case you haven't run into it yet, hashing is a mathematical function that creates a signature of a file or other data. In the case of cyber threat intelligence, if you identify a particular file as malicious, then you can share it's hash with others who can immediately block a file if they find the same hash.
File hashes are easy to share, easy to validate, and trivial for an cyber-criminal to adapt. Any change to a file, even adding a zero to the end, will change the hash. Adapting a file hash is therefore Influence Energy 1. If one of a cyber criminal's tools is identified via hash then it only takes knowledge representing 10 hours of learning to adapt it.
Important to note that sharing of hashing is Security Energy 1 which is effective against IE 0 threats who only have the capability to use public tools -- all of which have known hashes.
Climbing the pyramid, you get to "IP Addresses" and "Domain Names" which are associated with criminal infrastructure. Changing IP addresses associated with a malware campaign involves modifying virtual hardware and reconfiguring malware to use the new parameters. Coordinating all these changes is straightforward with roughly 10x the knowledge and effort of changing a hash (IE 2).
You might be wondering about cyber criminals with dynamic infrastructure that can change in a moment. Does that mean this would be Influence Energy 0 or 1? It would if the ability to create such dynamic infrastructure only took a few hours. Building such a system involves hundreds or thousands of hours between learning, building and testing. It is possible and the groups capable want to ensure their ROI.
Domain Names and IP addresses are also common threat intelligence, once they are associated with cybercriminal activity they can be blocked with Security Energy 2 capabilities.
Next up the pyramid are Tools and Artifacts. Artifacts are any files, registry keys, or logging formats created on a system after malware has run. Even if an IE 2 cybercriminal modifies their hash and modifies their IP address, without altering the malware tool itself, they will still leave the same footprints on their victim servers. Changing artifacts involves modifying how tools work which requires still more capability than changing IP addresses (IE 3).
Tools and artifacts are more difficult to defend against directly. It requires getting sufficient visibility into what is happening on affected systems. Security Energy 3 includes SIEM and enhanced logging capabilities which allow for this analysis.
Finally, at the top are Techniques Tactics and Procedures which are both the hardest to change (IE4+) and hard to defend against (SE 4+). For the cybercriminal, changing TTPs requires building entirely new capabilities with a high degree of understanding the goal. For the defender, detecting TTPs reliably involves tuned log analysis that take into account what's normal in your environment.
Take Credential Dumping (T1003) as an example. If an adversary has a method of accessing LSASS memory to read credentials, a high Security Energy org (SE4) with good visibility and tooling, could write a detection rule to find this. If the threat actor has IE4 or higher, they would have the ability to find a new way to access the credentials which does not trigger this rule.
At each level We can see the cat and mouse game of how to effectively use threat intel to defend and what cyber criminals need to move up. The energy of each side determines the who comes out on top.
David Bianco did the cyber community a great service by coming up with the Pyramid of Pain and Security Energy builds on this to provide actionable information for how to effectively use all forms of threat intelligence.
