Is Security Energy "yet another cyber framework?"
Yes, and it is complementary to others like MITRE ATT&CK and NIST. Cyber frameworks like these are limited by their attempt to be holistic. For example, MITRE ATT&CK states right up front that it is a "knowledge base of tactics and techniques based on real world observations." This means they are attempting to catalog every observed cyber threat technique. This is very useful for creating a language and taxonomy for cyber professionals to talk but ignores how likely or how much effort each technique may be.
Picture yourself as a child asked to set the table and given access to a huge cabinet full of dishes and flatware. Where do you start? Do you need one of everything? What if you break something? Similarly, telling someone new to security that they need to use MITRE ATT&CK to be secure is overwhelming.
The cybersecurity industry also likes to tell people "here are 97 freely available resources to learn about networking, build an open source SIEM, write alerts, and secure your website." Somehow giving someone a firehose of information is supposed to produce useful security outcomes.
Free resources are fantastic to motivated individuals who want to build up their skills and become super cyber security professionals…this is the bread and butter of who the community is today. What this lacks is a way to intelligently tell non security people what they need to do.
These people are used to hearing some version of "the cyber apocalypse is coming" or "everything is hackable." Such statements may sell a few more products at the cost of ostracizing large swaths of organizations who then focus on the wrong threats for their profile or worse, tune out entirely.
Security energy is a positive development that goes against this. It defines what works well against what threats and who should be worried about those threats. This is a roadmap for security.
It is inspired by elements of the DHS Commodification of Cyber Capabilities report which presents a threat framework termed the "Grand Cyber Arms Bazaar." This assigns levels of organizational maturity and operational intent to different threat actors.
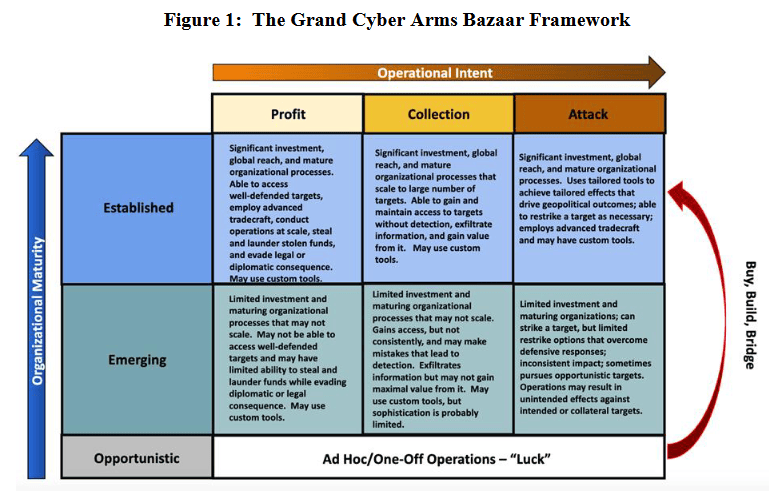
Influence energy takes this and quantifies it by assigning levels of resources (time and/or money) to each level and then breaking down which attack capabilities fit within each one. This is then matched in security energy with the defend techniques that are the appropriate countermeasures. An organization at Security Energy 5 needs to be prepared for nearly all MITRE ATT&CK techniques and yet another org at level 1 may only need to worry about a dozen. Either way, security energy gives organizations a specific roadmap for how to get to where you want.
On the other hand if you are building cyber products, Security Energy lets you stratify your product offerings in a threat-focused manner. You can then sell exactly the cyber security that each client needs.
It is the job of the cyber community to prioritize cyber threats and defenses so that organizations can optimize their defenses. Security Energy is process to get there.
